
In ALMALinux/Centos/RHEL 8, tcp_wrappers support was removed from the openssh daemon. This was already done sometime back in Fedora 28 release. Reasons given were as follows:
This was very useful 20 years ago, when there were no firewalls in Linux. This is not the case for today and connection filtering should be done in network level or completely in application scope if it makes sense.
While firewall rules can provide similar functionality but tcp_wrappers is still handy in some situations.
TCP Wrappers (also known as tcp_wrappers) is a host-based networking ACL system, used to filter network access to Internet Protocol servers on (Unix-like) operating systems such as Linux or BSD. It allows host or subnetwork IP addresses, names and/or ident query replies, to be used as tokens on which to filter for access control purposes. Let's do a bit of history first on the origins of tcp_wrappers.
The story begins in 1990 at Eindhoven University of Technology where Wietse Venama was administrator of the computer system network. Wietse is also the creator of the Postfix SMTP server. The university system was coming under increasingly heavy attacks from a Dutch computer cracker who was consistently able to gain root privilege. The cracker was skilled at typing the following command sequence:
rm -rf /
One night, Wietse noticed the cracker was watching him over the network, making contact with the finger network service. Since finger does not require a password, he was finally able to explain why much of the crackers activities had gone unnoticed. Wietse’s first reaction was to shutdown the finger network service. Instead, he decided it would prove more beneficial to maintain the service and determine where the finger requests were coming from. The solution he found was to make a swap by moving the vendor provided network server programs to another location, and install a trivial (TCP Wrapper) program in their place. Whenever a connection was made, the trivial program would just record the name of the remote host and then run the original network server program. The first TCP Wrapper version was just a few lines of code that Wietse carefully copied from an old network daemon source. Because it did not exchange any information with the client or server processes, the same TCP Wrapper version could be used for many types of network services. He made several improvement to the software and used to monitor the cracker activities. However the cracker was never caught. He maintained it until 1995, and on June 1, 2001, released it under its own BSD-style license.
The following attributes of TCP Wrappers are of prime importance:
- Wrappers can be installed without any changes to existing software, or to existing configuration files.
- The wrapper programs have no interaction with the client user.
- The wrappers have no interaction with the server application.
- Once the wrappers have established interaction between client and server, the wrapper disappears. Consequently, there is no overhead on either end.
In the previous version of Centos/RHEL before release 8, the openssh daemon, sshd had the libwrap library compiled in. This means the tcp_wrapper feature was supported and it worked in the following manner.
tcp_wrapper looks at the content of two files to determine access to network services:
/etc/hosts.allow
/etc/hosts.deny
rules in /etc/hosts.allow is processed first.
If you want to explicitly allow localhost full access and block 192.178.0.114 from accessing sshd, the contents of the two files are as follows
/etc/hosts.allow
ALL: 127.0.0.0/8
/etc/hosts.deny
sshd: 192.168.0.114
sshd because of the libwrap library will honor the hosts.deny entry and refuse ssh connection from the host 192.168.0.114. Any modification to the files will take immediate effect.
I have been using tcp_wrapper to block ssh brute force attacks. A background program watches the /var/log/secure for failed attempts to login via ssh. After 3 failed tries, the IP address of the attacker is entered into /etc/hosts.deny file and that attacking host is blocked instantly.
While this can also be done by creating a firewall rule to DROP/REJECT connection from this attacker. I find the tcp_wrapper approach to be simpler and I have a list of the offending IPs in one file.
This approached had work very well for many years until Centos release 8. The openssh no longer has the libwrap library. So I used Fail2Ban to block ssh brute force attacks instead. It will block the attacking IPs by creating firewall rules via firewalld.
Recently I wanted to try to find a way to use tcp_wrapper like mechanism to block ssh brute force attacks. After review some options I reread this link and it provided a way to incorporate tcp_wrapper support to sshd. In fact, the methodology is very similar to the approach used in the 1990s when Wietse implement tcp_wrappers.
The implementation is as follows:
Install tcp_wrappers
yum install tcp_wrappers
cd /etc/systemd/system/
cp /usr/lib/systemd/system/sshd@.service .
edit sshd@.service
CHANGE THIS LINE
ExecStart=-/usr/sbin/sshd -i $OPTIONS $CRYPTO_POLICY
TO
ExecStart=@-/usr/sbin/tcpd /usr/sbin/sshd -i $OPTIONS $CRYPTO_POLICY
IF SELINUX is enforced, this seboolean needs to be turn on
setsebool ssh_use_tcpd on
getsebool ssh_use_tcpd
ssh_use_tcpd --> on
Stop the current ssh service and start the sshd socket
systemctl stop sshd; systemctl start sshd.socket
To make it permanent remember to disable sshd.service and enable sshd.socket
the tcpd program will checks on the /etc/hosts.allow and /etc/hosts.deny (create them first) files before running the sshd program. Essentially the same tcp_wrapper functionality is back in place. I can now run my ssh brute force blocking program again.
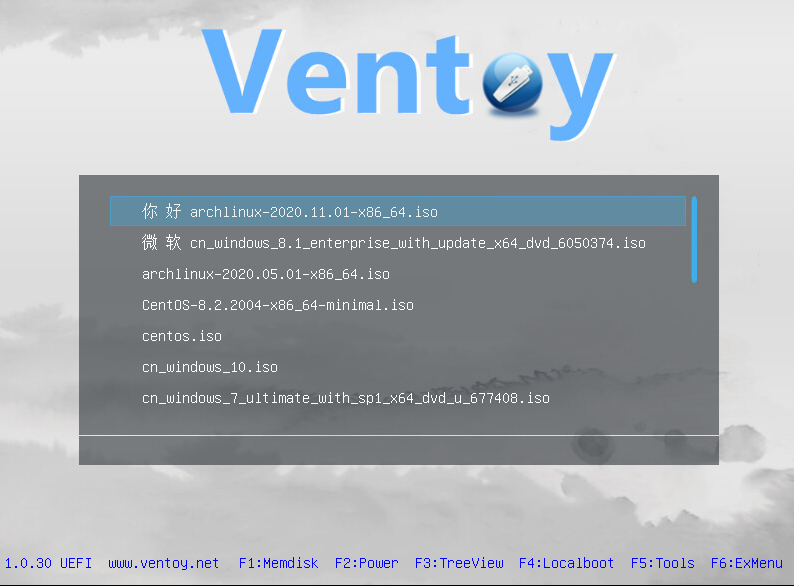
In past, I would make a bootable usb drive from the archlinux ISO for installation purposes and forget which I put it. On one occasion, I had a boot issue and needed to "rescue" the archlinux. Because I could not find the archlinux usb drive, I had to download the ISO and make another boot device.
This week I heard about a software tool called Ventoy from the Late Night Linux podcast. It will allow multiple ISO to reside in one usb drive and it will create a menu list upon boot for the user to choose the specific ISO to boot. It supports both Windows and Linux environments and the default filesystem it uses for the storage partition in the usb is the exFAT filesystem. Of course you can reformat this storage partition to any other linux file system of your choice. You just copy into the storage partition the ISOs and boot the usb drive to use any one of them.
One caveat is that only ISOs that support UEFI boot can be used. For example, this Ultimate Boot CD iso did not boot as it did not support UEFI boot.
Use a USB 3.0 usb drive for more tolerable boot speed and the appropriate size for all the ISOs you want to put in it.
Here is my list of ISOs for OS rescue, system test, partition sizing, disk cloning and general troubleshooting.
- Almalinux 8.4 RHEL 8.4 clone
- Centos 7 RHEL 7 clone
- Archlinux A very very up to date linux distribution
- Rescatux is a Debian-based live distribution featuring a graphical wizard for rescuing broken GNU/Linux and Windows installations and boot loaders.
- SystemRescue Archlinux based rescue toolkit.
- Gparted Manage disk partitions ( create,delete, resize, copy, and move partitions without data loss)
- Clonezilla is a partition and disk imaging/cloning program similar to True Image® or Norton Ghost®. It helps you to do system deployment, bare metal backup and recovery.
- PCmemtest memory tester is based on a fork and rewrite of Memtest86+
 The Centos Linux distribution was first released in 2004. It fulfilled its promise as a free and binary compatible version of RHEL ( Red Hat Enterprise Linux ). The project is possible because the source code for all the software in RHEL is publicly available. The Centos project folks will strip out any RedHat copyright information and recompiled to create the binary RPM packages. All the packages are bundled together into a Linux distribution that was easy to install.
The Centos Linux distribution was first released in 2004. It fulfilled its promise as a free and binary compatible version of RHEL ( Red Hat Enterprise Linux ). The project is possible because the source code for all the software in RHEL is publicly available. The Centos project folks will strip out any RedHat copyright information and recompiled to create the binary RPM packages. All the packages are bundled together into a Linux distribution that was easy to install.
Centos is a popular distribution because it mirrors RHEL and provides the corresponding software updates. It has the same 10 years of support life span as RHEL. It has also been incorporated into many commercial software/hardware products.
In Jan 2014, Red Hat announced their hiring of the Centos team and acquisition of the Centos project. Centos still maintained its independence from Red Hat with its own governing board. This change was positive as it gave financial stability to the Centos team and helped to keep the Centos distribution and update releases on a consistent pace.
IBM acquisition of Red Hat closed on July 9, 2019. It was in no doubt that there will be changes coming. In December 2020, Red Hat unilaterally terminated CentOS development. Red Hat will however continue to support the related rolling release distribution called CentOS Stream.

Centos 8 will ceased to be supported on 31st December 2021. CentOS Stream is replace it but it will no longer be one to one compatible with RHEL 8. Software will be changing all the time and eventually it will become the next RHEL release. In the development cycle, CentOS Stream will be positioned between Fedora and RHEL. CentOS Stream will not be suitable for production use due to the software changes. To put it plainly, Centos Stream is like a RHEL Beta which will used for developing new features for the next RHEL release.
The Centos user community was incensed on hearing this announcement. Those who have implemented Centos 8 were placed in a untenable position because instead of a End of Life date of May 2029, Centos 8 support will end in 1 years time.
Subsequently 2 projects were started to provide a replacement to Centos 8.
Rocky Linux

Almalinux

Rocky Linux is led by Gregory Kurtzer, founder of the CentOS project. The current ETA for a beta release is April 30th.
Almalinux is a project run by The AlmaLinux OS Foundation. Cloudlinux Inc backs the Almalinux project. Cloudlinux Inc makes a Linux distribution CloudLinux OS marketed to shared hosting providers. CloudLinux OS is based on the CentOS operating system; it uses the OpenVZ kernel and the rpm package manager.
Rocky Linux starts from ground zero however Almalinux is being worked on by a team that has already produced a fork of RHEL 8 for CloudLinux OS.
On Mar 30 2021, Amalinux 8.3 was officially released. On Mar 31, using the migration script provided almalinux-deploy. I successfully did a inplace switch to Almalinux from Centos 8. After the script performs a few initial checks, it began the process of removing, reinstalling, downgrading, and upgrading certain packages in order to synchronize the system with the current AlmaLinux release. The entire process took about 20mins which concluded by rebooting the system.
Almalinux being 1::1 compatible, everything works. Already there features that it provides which was missing from Centos. Almalinux maintains the errata information in their repositories. Therefore you can retrieve only updates related to security or perform queries based on types of errata.
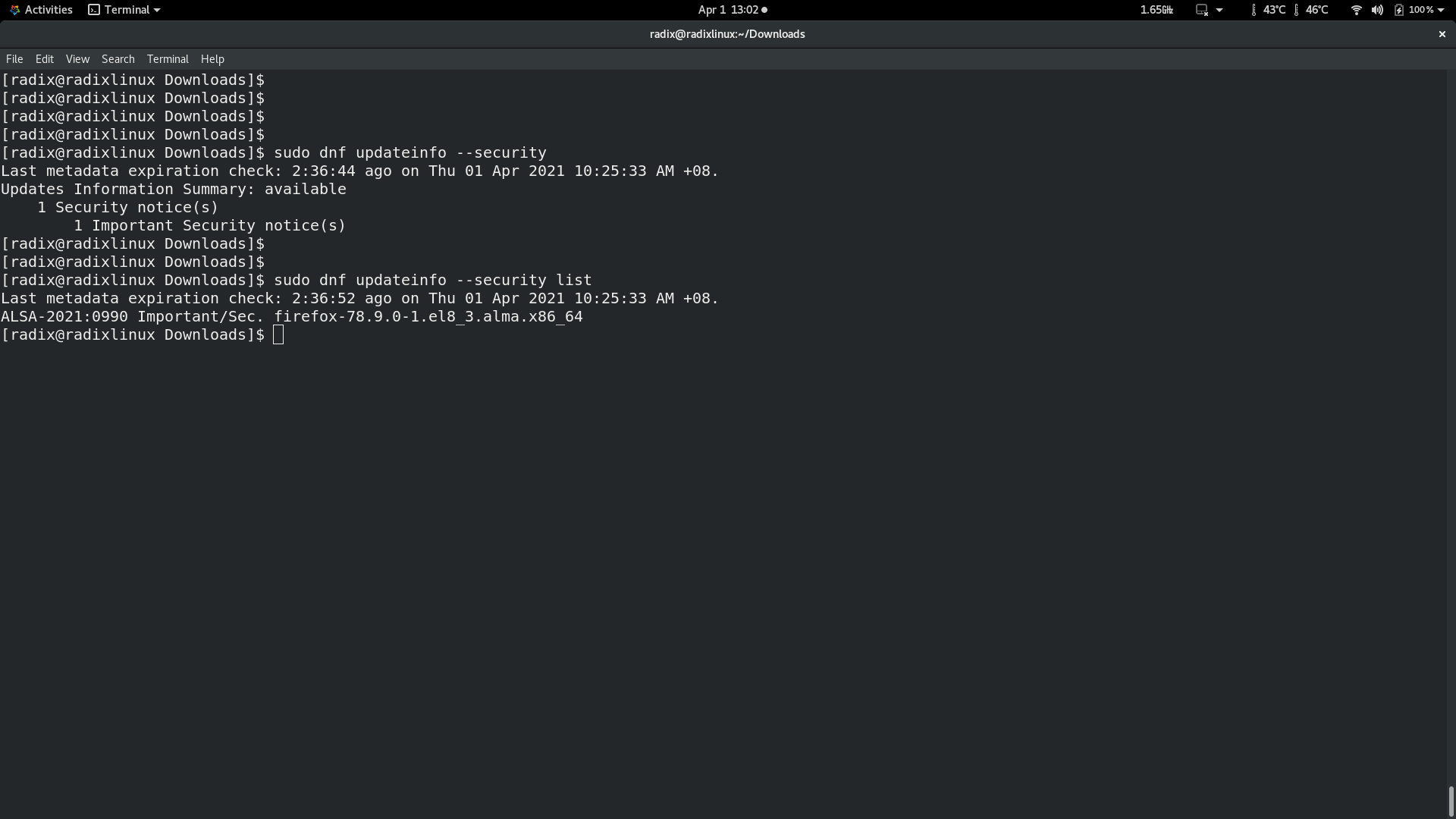
The other observable improvement is the speed of updates. Two recent flaws have been found in openssl, which were deemed important. Redhat patched their source code on March 24-25 and released openssl packages for RHEL8 on March 30.
AlmaLinux had updated openssl packages by March 31st. Centos will probably take awhile longer to release their updates. To be fair, Centos will provide quick update responses for critical security patches.


 The Centos Linux distribution was first released in 2004. It fulfilled its promise as a free and binary compatible version of RHEL ( Red Hat Enterprise Linux ). The project is possible because the source code for all the software in RHEL is publicly available. The Centos project folks will strip out any RedHat copyright information and recompiled to create the binary RPM packages. All the packages are bundled together into a Linux distribution that was easy to install.
The Centos Linux distribution was first released in 2004. It fulfilled its promise as a free and binary compatible version of RHEL ( Red Hat Enterprise Linux ). The project is possible because the source code for all the software in RHEL is publicly available. The Centos project folks will strip out any RedHat copyright information and recompiled to create the binary RPM packages. All the packages are bundled together into a Linux distribution that was easy to install.


